Online Backup With Versioning Your Best Antidote
The CryptoLocker virus/malware/ransomware is one of the worst infections your PC can endure. And while the infection often is effected by a bogus email with an attachment the threat they follow up with is real.
CryptoLocker really does encrypt your files and you will NOT be able to decrypt them without paying the ransom. But paying the ransom is NOT recommended, even though some seem to have gotten their files back this way since further infection of a worse kind is not only possible but probable with the solution they sell you.
Does An AntiVirus Program Protect Me?
In a word, no, an antivirus program will not protect you from CryptoLocker. The malware comes in just too many constantly mutating forms to expect absolute protection from any of the top antivirus software programs. Behavioral monitoring by some of the more advance A/V programs can stop it, but no guarantees.
Does that mean you should not bother with and antivirus program? NO, please DO install a quality antivirus, antimalware solution and make sure they are keeping themselves updated (sometimes a bug will cause an antivirus program to stop updating itself – which is a bad thing.
I Backup To A Local USB Drive, Am I Safe From CryptoLocker?
The only way your backups to a local USB drive would help you recover from CryptoLocker is if you DISCONNECT the USB drive AFTER the last backup BEFORE CryptoLocker hit. Otherwise, the files on your USB drive or even a network drive would likely be encrypted for ransom as well.
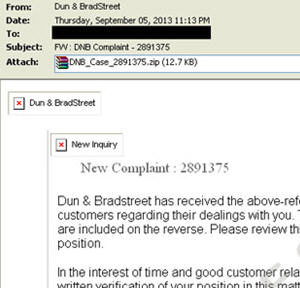
The CryptLocker Warning Banner
Usually, once infected, CryptoLocker will work in the background and quietly encrypt all of your files without placing too noticeable of a load on your PC. Then, once it is too late for you to do anything about it, they will display this red warning banner:
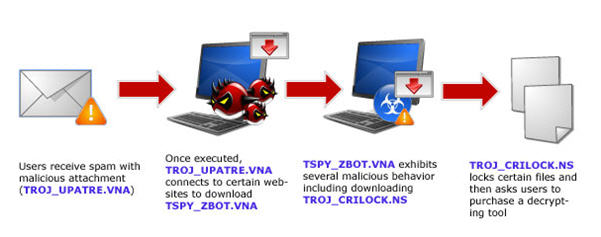
How CryptoLocker and Similar Ransomware Work
In most cases, CryptoLocker and for that matter, all viruses and malware can be avoided with wise user practices like not opening email attachments unless you know who they are from AND ARE EXPECTING THEM. You cannot open an attachment just because it’s from someone you know because it could be that their computer is compromised and sending malware to everyone in their address book.
Also avoid suspicious websites or those associated with ‘questionable’ content like porn, free downloads, etc. Always avoid those free holiday screensavers.
Below is a diagram courtesy of Trend Micro Security, makers of Trend Micro Titanium Maximum Security
 The Only True Protection Against CryptoLocker Ransomware
The Only True Protection Against CryptoLocker Ransomware
Unfortunately the only true way to protect your data against ransomware is to have a quality Online Backup software like IDrive protecting your files by backing them up to your cloud storage account AND having multiple versions (30 in the case of IDrive) such that once your files are encrypted by CryptoLocker, yes they will get backed up to the cloud – though it will take a while before they all are – and that could be a warning sign too!, but you can restore to your PC AFTER it’s been cleaned, a previous version that has NOT been encrypted by the ransomware.
Prevention Of Ransomware Like CryptoLocker
Here are some tips for PREVENTING ransomware from taking your files hostage:
- When a computer in your home or office becomes infected, isolate it IMMEDIATELY by pulling the network plug and disconnecting any USB devices to help further infections or encryptions
- Avoid opening any email attachments that are not expected
- Avoid visiting un-trusted sites that may redirect or download this malware into the system
Above all, though, make sure you have unencrypted backups out of reach from the malware in a secure cloud backup solution.
IDrive is our #1 pick and what I have installed on the computer I am writing this post on.




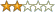
3 Comments